[Image: KAUST]
While still far from practical implementation, the prospect of ultra-powerful quantum computers has raised significant concerns about information security. That’s because a true quantum machine could quickly undermine the classical security protocols on which the current e-commerce edifice is founded, potentially bringing the whole thing crashing down.
That prospect has spurred remarkable progress in the technology of quantum key distribution (QKD), an information-security approach that, in principle, could straight-arm the security threat from quantum computers. But QKD networks, relying on delicate single-photon processes, face some knotty problems in scalability, speed and bandwidth. Now, researchers in Saudi Arabia, the United Kingdom and the United States claim to have devised an alternative to QKD that can achieve “perfect-secrecy cryptography” through 100% classical channels—and that’s compatible with the existing optical-communications infrastructure (Nat. Commun., doi: 10.1038/s41467-019-13740-y).
Blast from the past
The new security protocol proposed by the research team, led by OSA Fellow Andrea Fratalocchi of the King Abdullah University of Science & Technology (KAUST) in Saudi Arabia, rests on a very old model: the one-time pad (OTP). First proposed by Frank Miller in 1882, during the age of telegraphy, and later patented in 1919 by Gilbert Vernam, the OTP involves the creation of a unique, random one-time key that’s the same length as the message being encrypted, and that’s added to the message.
In a classic 1949 paper on information security, Claude Shannon proved that the OTP (sometimes called the Vernam cipher) is absolutely unbreakable if properly implemented. And therein lies the problem: It’s been quite difficult to find ways to practically and securely exchange the OTP key between communication nodes in the real world. (Indeed, the “pad” part of one-time pad refers to some early implementations in which the key was distributed on a pad of paper, with the top sheet destroyed after each use—a system hard to imagine in an era of remote, split-second internet communications.)
Leveraging chaos and the second law

Andrea Fratalocchi of King Abdullah University of Science and Technology (KAUST), Saudi Arabia, led the research team. [Image: KAUST]
Fratalocchi’s team sought to set up a version of the Vernam cipher that could take advantage of the wide bandwidth and existing infrastructure of optical communications, without an overlay of special equipment and processes for quantum key distribution. The scheme the researchers have come up with draws on two familiar themes: the physics of chaotic systems, and one of the most resolutely classical of principles, the second law of thermodynamics.
In the team’s approach, two communicators—“Alice” and “Bob,” figures familiar to any reader of the quantum-security literature—each are equipped with an optical chip. The chips include scatterers that generate chaotic light states (random superpositions of classical optical waves at different frequencies) and whose configuration can be structurally and irreversably modified after each communication, making each chaotic light state unique. The mixture of the two chaotic light states generates a key that is used to encode and subsequently decode the data (through a bitwise exclusive-or, or XOR, operation), following the Vernam-cipher protocol.
Under the scheme, an eavesdropper (“Eve”) could, in principle, intercept the communication, access all information about the system, back out the initial conditions used to create the light states she intercepted, and re-create the key. But the irreversible processes used by Alice and Bob to change the chips after each communication create “new chaotic structures exponentially different from the ones used in the communication” that Eve intercepted. That increases the system entropy; Eve can only reverse the thermodynamic transformations wrought by Alice and Bob through a decrease in entropy, which would violate the second law.
Fingerprints and billiard balls
As a proof of concept, the researchers took digital images of human fingerprints, and used them to create optical chips with reflective nanodisks that act as point scatterers along the fingerprint contours. The scatters together form a chaotic microresonator, in which an input light field bounces around like a billiard ball amid the scatterers, with the dynamics becoming chaotic after a few collisions.
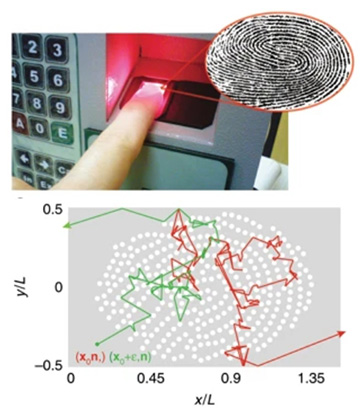
In the team’s proof of concept, digital scans of fingerprints (top) were used to create chaotic microresonators, with arrays of reflecting nanodisks that scattered light in chaotic, billiard-ball fashion. [Image: A. Di Falco et al., Nat. Commun., doi: 10.1038/s41467-019-13740-y (2019); CC-BY 4.0]
For purposes of the experiment, the chips could be changed after each communication, as required by Vernam cipher, by depositing a non-purified drop of water, which introduces additional scatterers. (In commercial implementations, the team envisions the same function being achieved by the use of dynamically deformable media such as hydrogels doped with solid-state scatterers.)
The team tied the prototype chips together using single-mode optical fiber, and used the chips to chaotically encode and successfully decode communication of a moderately complicated image between Alice and Bob. The eavesdropper Eve, attempting to hack into the communication with complete knowledge of the system and using all of the same equipment, obtained only white noise in her decoded image. The team also validated the experimental system “for real-world applications” against a suite of statistical tests from the U.S. National Institute of Standards and Technology (NIST).
A scalable alternative to QKD?
The researchers note that the system requires no sustained “electronic databases, private keys, or confidential communications” after initial authentication of the users, and rests on “the technical maturity, speed, and scalability of classic optical communications.” Those properties, they argue, make their approach an “open pathway towards implementing perfect secrecy cryptography at the global scale with contained costs.” The authors have filed a provisional U.S. patent application on the method.
“Implementing massive and affordable resources of global security is a worldwide problem that this research has the potential to solve for everyone, and everywhere,” team leader Fratalocchi argued in a KAUST press release accompanying the research. “If this scheme could be implemented globally, crypto-hackers will have to look for another job.”
In addition to researchers at KAUST, the project included contributions from scientists at the University of St. Andrews, U.K., and the Center for Unconventional Processes of Sciences, USA.
